Denial of Service (DoS) Protection
Safeguard your revenue and reputation
Denial of Service (DoS) attacks attempt to block your organisation’s legitimate traffic, causing downtime, service disruption and lost revenue.
Attacked hosts can become overwhelmed - knocking out your website, email server, VPN, phone system or office Internet connection.
hSo's DoS Protection fixes this by filtering out bad traffic upstream using industrial-scale hardware.
Why choose hSo for DoS Protection?
Threats stopped in cloud
hSo filters out attack traffic before it can overwhelm your firewall or saturate your Internet connection.
Affordable pricing
You just pay a fixed monthly fee that covers all attacks regardless of their size.
24/7 monitoring
hSo’s DoS Protection service complements the proactive, 24/7 monitoring service that we provide for our customers’ networks
Protect revenue & reputation
Downtime is as frustrating for customers as it is costly for businesses. Protect your firm against this damage.
No hardware
There’s no hardware to buy or configure, as our DoS Protection service is cloud-based.
Normal traffic unaffected
Scrubbers pass clean traffic on to your network, so you can stay online even when under attack.
Additional Benefits
Scale of protection
Our service has robust DoS mitigation capacity, ready to combat attacks of up to 1 terabit per second (1 million megabits per second).
Stay in control
As soon as hSo’s monitoring system identifies an attack on your network, we'll let you know. We'll implement appropriate attack mitigation strategies, consulting you as we do.
How hSo's service works
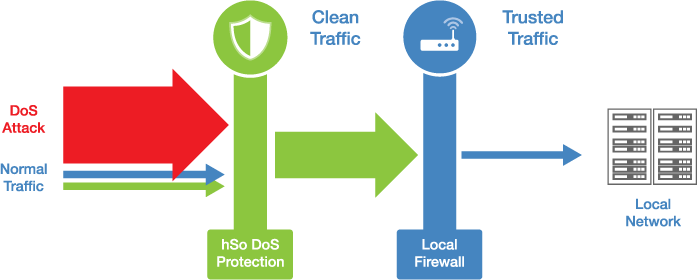
What exactly is a Denial of Service attack?
It's a cyber attack where unhelpful traffic is sent to the internet-facing bits of your IT with the intention of overwhelming the hardware or connectivity, so legitimate traffic can't get through.
Typically, an attacker might target your web site, your email server, your office firewall, your VPN gateway, your office phone system's gateway or your DNS servers.
Using local firewalls to mitigate DoS attacks is not effective. The reason is that by the time traffic has hit the local firewall and is being discarded, it has already flooded the connection and is blocking any legitimate traffic from reaching the firewall.
A Distributed Denial of Service (DDoS) attack is a form of DoS attack that uses numerous devices and Internet connections, often dispersed into a botnet. A DDoS attack is more difficult to thwart as the target is inundated with requests from so many sources.
Many DoS attacks, for example Teardrop and Ping of Death attacks, capitalise on weaknesses in the TCP/IP protocols. In a similar way that new viruses are constantly being created by hackers, new types of DoS attacks are always emerging. Motivation includes competitive damage and blackmail.
Get in touch
020 7847 4510
We may process your personal information in order to send you information you request, measure and improve our marketing campaigns, and further our legitimate interests. For further details, see our privacy policy.
Contact us
-
- Head Office:
- hSo, 50 Leman Street, London, E1 8HQ
- Switchboard:
- 020 7847 4500
- Support (24x7):
- 0333 200 3337
- support@hso.co.uk
- Marketing & Sales:
- 020 7847 4510
- info@hso.co.uk










